System Overview
SaaS Provider Model
BluBØX provides hosted services using the Software as a Service (SaaS) model. Software-as-a-service (SaaS) is a software licensing and delivery model that eliminates the need for individual entities to purchase, deploy and maintain IT infrastructure or application software. SaaS vendors are able to amortize their infrastructure costs over thousands of users yielding lower total costs of ownership (TCO) for customers. This ability to amortize costs enables SaaS vendors to make investments that guarantee the security and resiliency of their solutions that would not be viable for many business customers.
Advantages of the SaaS model for physical security include:
• No dedicated on-premises computer equipment and software to maintain
• Access to superior technology at a lower Total Cost of Ownership (TCO)1
• Continuous maintenance and upgrades are included with the service
• Ability to rapidly scale and modify service levels on demand
• Simple and secure access to your system anytime and anywhere
• Shifting workload to the SaaS provider allows you to focus on your business
Basic System Operation
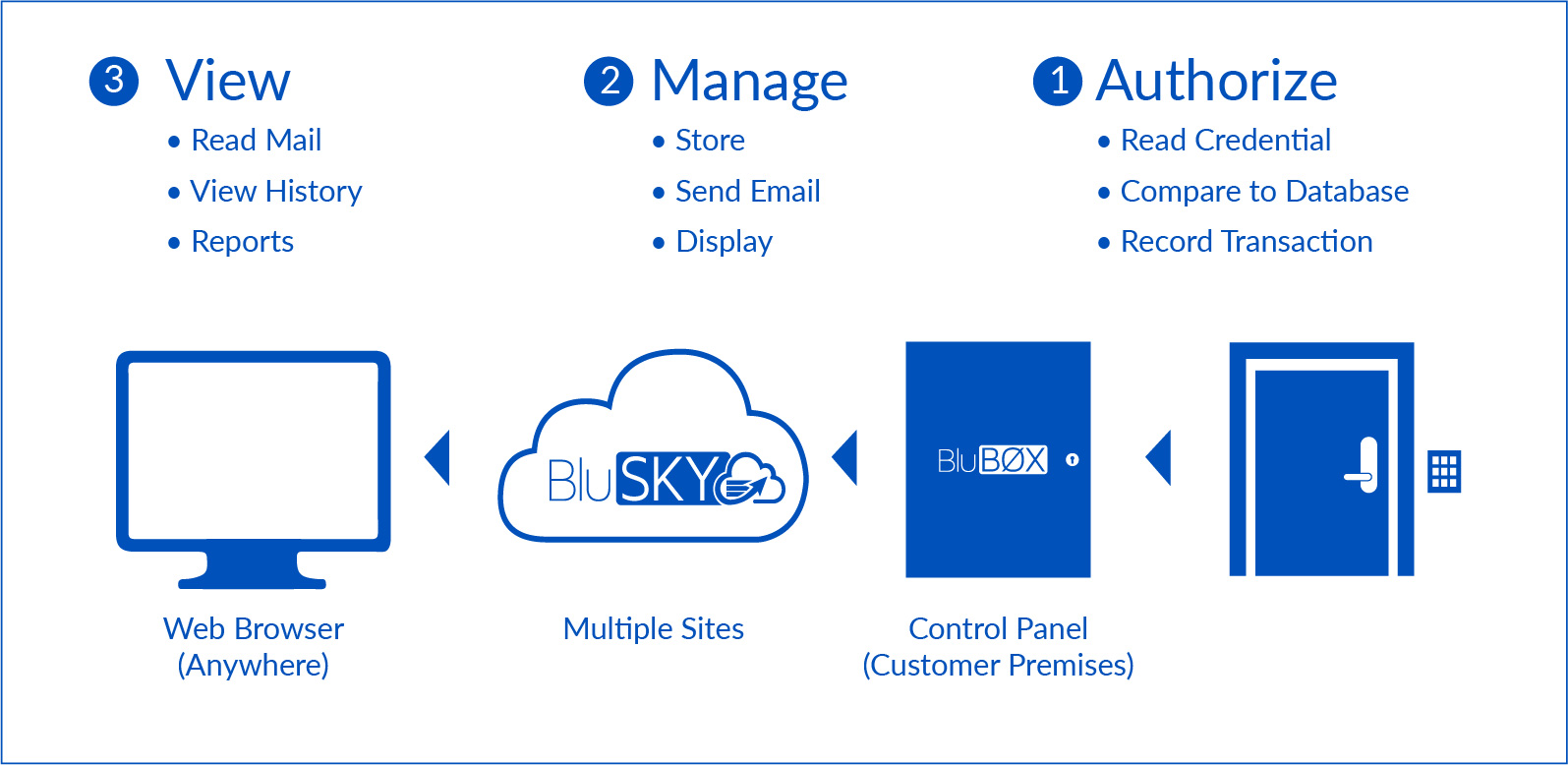
As shown above in Figure 1, there are four major components to the overall operation of the BluSKY® service:
• Customer premises equipment (control panels, credential readers, cameras)
• Network communications via Internet
• BluBØX’s centralized, cloud-based applications resident at our data centers
• Web browser on the end-user’s PC or mobile device
These components share data across multiple platforms and networks in order to manage access control privileges, deliver alarm and event records, and to provide other services such as software updates to control panels.
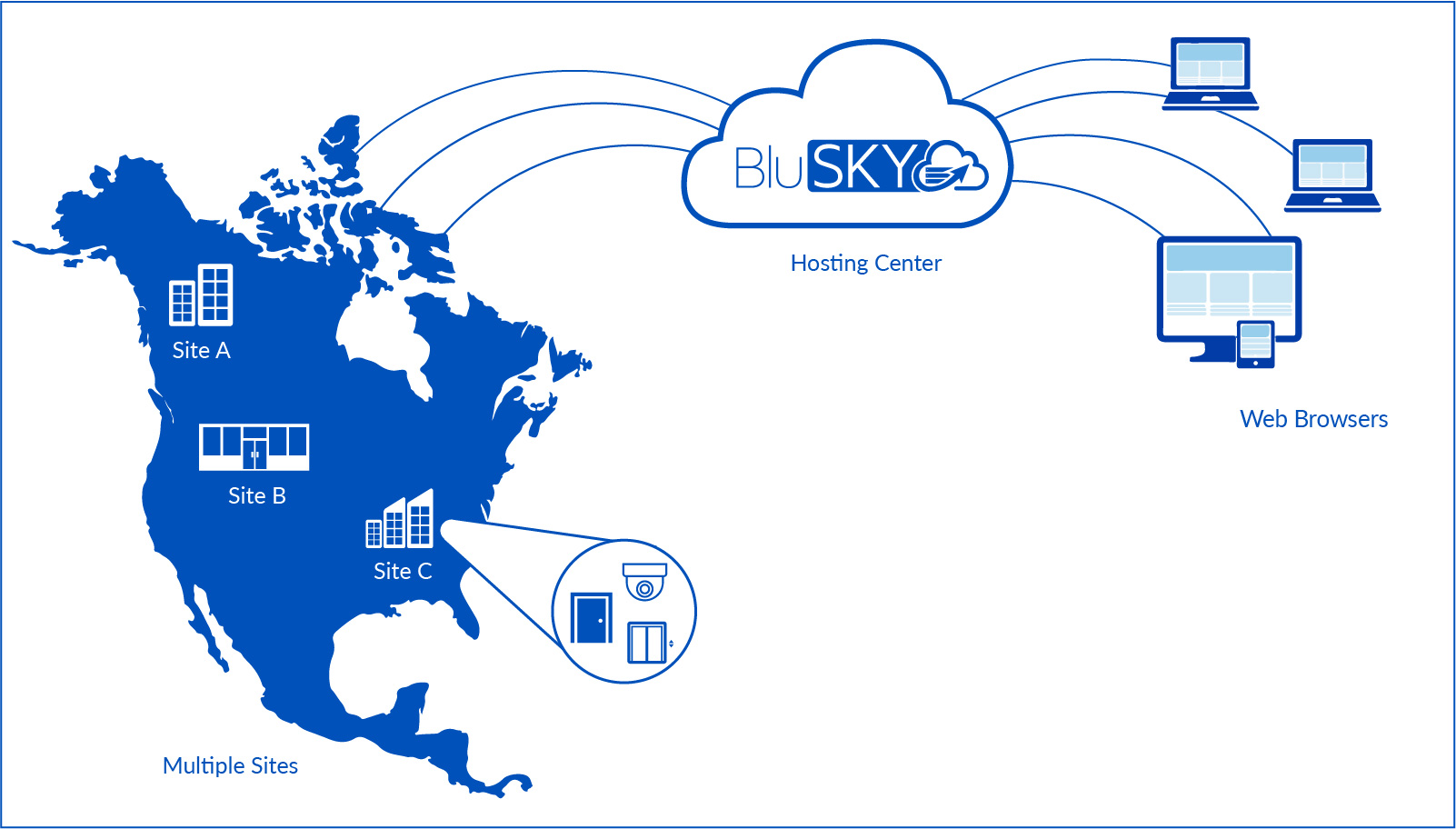
Control panels are networked to our data centers through a variety of technologies, both wired, and wireless. Wired options include a built-in Ethernet port for connection to a corporate LAN, or broadband modem, or any other IP-based networking technology with connectivity to the Internet. Wireless networking options include a cellular network router. Alternatively, sites with a wireless 802.11 network may use a wireless bridge to the control panel to simplify wiring requirements.
Data Life Cycle – Creation and Distribution
The access control life cycle begins with an administrator logging into BluBØX’s application and setting up users, groups, credentials, schedules, and other security policy elements that dictate who has permission to enter which facilities at which times. Security policy data is stored centrally and then distributed to the control panels where policy rules determine access to each connected door. When policy changes are made, updates are pushed to the panel immediately. Maintaining a local copy of the security policy allows a panel to operate even if temporarily disconnected from the internet. When connectivity is restored, any changes to the security policy are immediately applied.

Data Life Cycle – Access Event Notification
Control panels manage access to doors by comparing the credentials acquired by a reader (e.g., proximity cards, PIN codes, fingerprints, mobile credentials, etc.) with a local database of credentials. When a person presents a credential to a reader attached to a BluBØX control panel, the panel makes a comparison against its database to determine whether access is allowed at that door, at that particular time.
The control panel then grants or denies access, and immediately sends a transaction record to the data center which can then be viewed or searched. After this transaction record has been received at the data center, BluBØX’s application software stores the information for subsequent customer viewing and reporting.
The software can associate business rules with these transaction types, and can take action based on observing transactions being reported. A common use of this capability is to request an email notification when a particular type of event is observed. The application sends an email notification to a list of addresses set up for notification on the account. These transactions are also available to administrators via our BluSKY Mobile Application.
Of course, all of these transactions are handled securely. The next section of this paper introduces some Internet security basics, the building blocks for ensuring that all BluBØX customer data remains protected.